Spidr ZTM Reference Guide
This guide provides an overview of Spidr's "Zero Touch Monitoring" (ZTM) tool: our proprietary software designed to facilitate fraud and risk oversight at both the customer and transaction levels. Whether you're still in the process of selecting fraud vendors, or you're considering integrating ZTM into your system, feel free to reach out to a Spidr team member for more information and assistance.
Overview
ZTM facilitates comprehensive fraud detection and decisioning and seamlessly integrates with Spidr's unified data model to simplify your operations (more info on the unified API here).
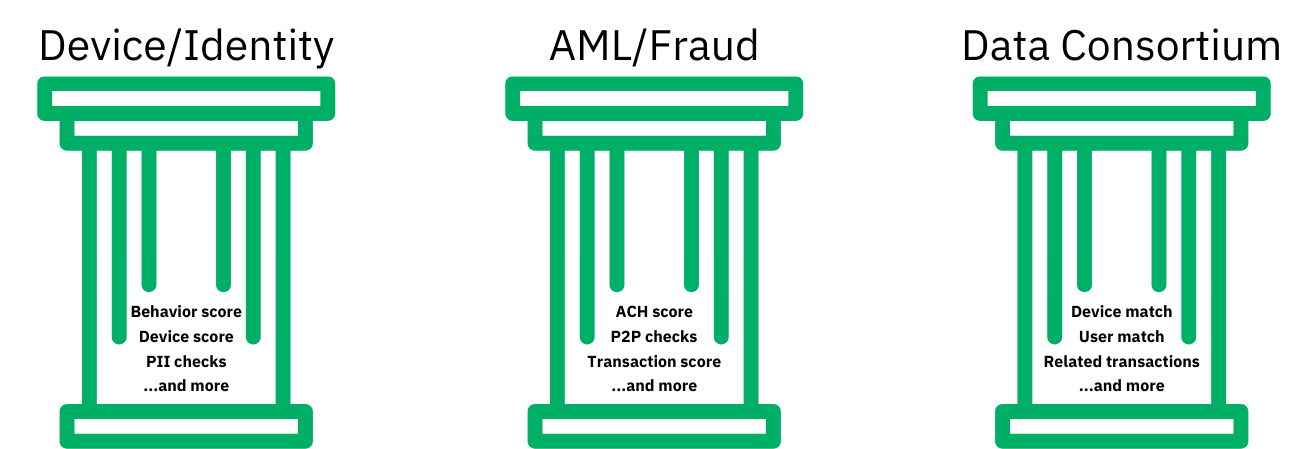
ZTM is built on three core pillars: device and identity checks, "Anti-Money Laundering" (AML) and fraud monitoring, and data comparisons against a consortium of customer/transaction information. The ZTM API consolidates disparate information regarding customer attributes and behavior and returns an easy-to-digest risk score to help in your decisioning. All data sent through ZTM is linked to a Spidr unified user record, enabling full visibility into the customer lifecycle.
Why Use ZTM?
The fraud and risk landscape can be tricky to navigate, even more so without a solid set of tools to help you respond. Although you have the freedom to bring in your own fraud and compliance vendors with Spidr, integrating with ZTM ensures that your data is protected, enriched, and that you have all the context needed to make effective decisions.
Since ZTM integrates with the Spidr unified data model, it provides a single source of truth for managing risk. ZTM also can also greatly simplify operations by:
-
Serving as a single integration point for your app
- 🙅Without ZTM: A typical fraud and risk set up will require multiple integration points with different vendors. You have to juggle API keys, separate webhook endpoints, and the quirks of using each system.
- ✅With ZTM: ZTM is powered by data from best-in-class vendors in the fraud and risk space. You get all the benefits of multiple data sources and comprehensive data sets without having to manage the complexity. Set up a single webhook endpoint, create a session, and you are off to the races 🏇.
-
Providing context to your data
- 🙅Without ZTM: Managing separate identifiers and keeping your data in sync can be a pain. Likewise, it's often difficult to track all the customer interaction points when using separate systems.
- ✅With ZTM: Since ZTM data is attached to a Spidr unified user record, you'll never have to worry about using different identifiers or wrestling with different data types or objects. You can easily track your customer's journey and data in one place.
-
Saving you time and money
- 🙅Without ZTM: With others you'll have to worry about upfront costs and the ease of accessing quality support.
- ✅ With ZTM: If saving money without sacrificing quality matters to you (and we suspect it does), ZTM is the ideal choice. Through Spidr's partnerships with the aforementioned best-in-class vendors, we can offer ZTM at a price that beats any direct integration. Additionally, there's no upfront cost. ZTM support is second to none; we offer direct live support with agents who are familiar with the fraud and risk domain.
ZTM Use Cases
ZTM checks can be run on any type of customer interaction with your system. Whether it’s logging in, signing up, or linking a bank account, you can trust that ZTM can monitor every action.
ZTM is also fully modular, allowing you to customize rules and use cases to best fit your needs. Regardless of the use case, ZTM will always run device/behavior checks to ensure authentic customer behavior. See below for common ways to use ZTM.
| Use Case | Category | Description |
|---|---|---|
| Onboarding/KYC | Identity Fraud | ZTM will check the customer's device, "Personally Identifiable Information" (PII), and behavior/interaction with your system to ensure that they are authentic. |
| Bank linking | Funding Fraud | ZTM will validate the riskiness of the linked bank account. |
| ACH transactions | Funding Fraud | ZTM will run checks against the bank accounts involved and the transaction amount/details. |
| Peer to peer transfers | Funding Fraud | ZTM will run checks based on the source and destination account and transaction details. |
| Card transactions | Card Fraud | ZTM will score transactions based on their riskiness, taking into account prior customer behavior. |
How Does ZTM Work?
As mentioned above, ZTM can be used to inform your compliance decisions depending on your company's fraud and risk tolerance. As part of your ZTM integration, you'll set up a series of rules to define risky scenarios and manual review paths. The results of these rule executions, an overall risk score, and data signals will be returned in each ZTM response.
You can run ZTM checks on any flow inside your application, using the scores returned to make automated decisions or escalate for manual review in the ZTM dashboard. Any decisions made in the dashboard will fire off corresponding webhooks for you to ingest and parse per your business logic. For a sample end-to-end flow, see below. More information on the ZTM API can be found via our integration/API guide (reach out to a Spidr contact for more details).
With the basics covered, let's dive into a summary of each of Spidr's core pillars to better understand how ZTM works.
Device and Identity
ZTM uses a combination of device and identity scores to sniff out bad actors. It analyzes patterns in behavior, device characteristics, location anomalies, and personal information to flag suspicious activities and persons.
Device Checks 📱
- Device Identification and Signals - ZTM assesses whether the device is genuine (not spoofed) and determines the overall risk level based on device reputation.
- Behavioral Analysis - ZTM monitors user interaction with the device to detect unusual patterns, especially deviations from a user's typical actions. This can be helpful in monitoring for account takeover scenarios.
- Bot Detection and Location Analysis - ZTM looks for location discrepancies and bot-like behavior.
Identity Checks 🧑🦱
- Address and identity matching - ZTM weighs whether the information provided matches previous records/data sources available for the customer.
- Risk signals - ZTM calculates the risk associated with the provided PII (e.g. email, address, Tax ID) based on data provided by our partners.
- Sanctions and Adverse Media - ZTM can screen for matches with sanctions lists, "Politically Exposed Persons" (PEPs), and adverse media to assess reputational risk and guard against fraud.
AML/Fraud
All banking partners require an AML plan. Any transactions passed through ZTM are risk-scored to help protect you from risky money movement. Using these scores, you can reject, approve, or send transactions to manual review. The following types of transactions and transaction events can be scored:
- Direct deposits
- Bank linking
- ACH transfers (both credit and debit)
- "Card to Card" (C2C) or "Peer to Peer" (P2P) transactions
- Card transactions (both online and at point of sale)
ZTM can perform counterparty checks to verify the source and recipient of a transaction and will analyze each transaction to look for patterns and suspicious activity.
Data Consortium
ZTM leverages customer data from our partners and clients to build a fraud data consortium that enhances protection against bad actors. By cross-referencing individual customer data points across the consortium, we can identify suspicious behavior. Combining PII with “digital identity” markers—such as device, phone number, and email address—ZTM helps detect cases where customers may have a higher likelihood of engaging in fraud.
End to End Example
Still here? Awesome:partying_face: let's see what a typical onboarding flow would look like with ZTM
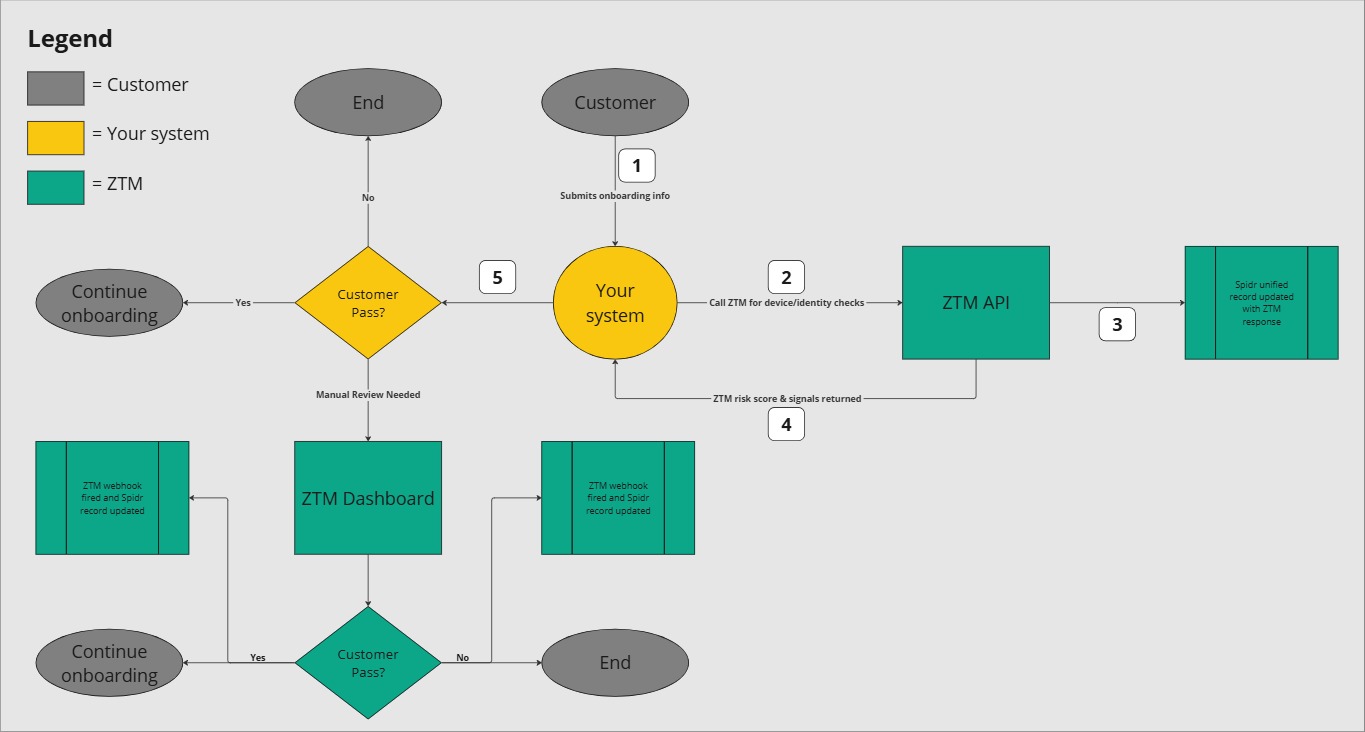
Example onboarding flow using the ZTM API and dashboard
Updated 5 months ago
If you have enrolled in ZTM, check out our integration guide. If you'd like to learn more about Spidr's unified API, you can review our 'Spidr Client Reference Guide'